If you’ve ever had a WordPress website and discovered that you can’t access updates anywhere (Update the core or update plugins), then most likely you have been the victim of hacking. Typically, it’s not a real person that has hacked your website. It’s a series of bots that go out and search WordPress websites (because it’s one of the most common platforms on the internet) and inject the PHP code with a string that gives hackers access to the website.
What it Looks Like
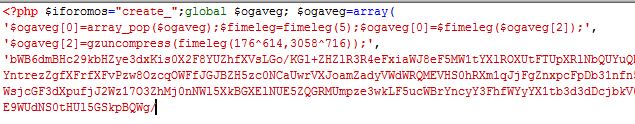
- The hack is basically just a single piece of code at the top of TONS of pages within your WordPress website. Here is a sample of what it looks like:

- Location of Code: The code that is affected is normally in the following folders:
- wp-admin
- wp-content/uploads
- wp-content/themes/[your active theme]
- wp-content/plugins
- [root folder]
- You might find it in a dozen files, but most likely you’ll find it in dozens if not hundreds of files.
Why They Do It
- Because they can.
- Because it allows them to leverage your hosting power for themselves
How They Do It
- The bots (software) are designed to submit special (injection) code into a form or known uploading exploit in your PHP website. It then allows the bot to write a single string (peice of text) in your source code at the top of your PHP pages.
- The string at the top basically disables your ability to do anything administrative to your website and also provides a backdoor for the hacker’s software.
How To Clean It
Ok, so this part is a little trickier. I’ve literally cleaned dozens of websites with these injections. Because of the number of files affected, the only effective way to clean it is to follow the directions below.
- Download (using Filezilla or another FTP application) the entire site into a temporary folder on your local computer
- Using Dreamweaver or another HTML editor of your choice, open several of your PHP files until you find a string like shown above. It’s always at the top of the page right after “<?php” and normally has something like “$iforomos”, “$ogaveg” or “$fimeleg=fimeleg(5)” and has an enormous string of nonsense characters and ends with something like “unset($ogaveg);”
- Highlight the entire string AFTER “<?php ” and copy it.
- Do a “Find and Replace” in the entire site, replacing that string with nothing.
- Re-upload all of the files to your website, ensuring that you are overwriting the files.
- All done!
How To Prevent It From Happening Again
The only solid way is to keep an eye on your website. Login regularly. Also, I would highly advise you to install a Web Application Firewall plugin like Wordfence (which is free), so that you are notified if anything does try to alter your website.